SANS: FOR572 & Passing the GNFA!!!

My review of SANS FOR572 training and GIAC's Network Forensic Analyst certification exam.
Published on April 19, 2021 by Tony E.
sans giac certifications network forensics
6 min READ
GIAC: Network Forensic Analyst (NFA)
tl;dr This is not a humble brag but if you have good experience and are a professional in at least 1 or more related fields, it might not be too difficult.
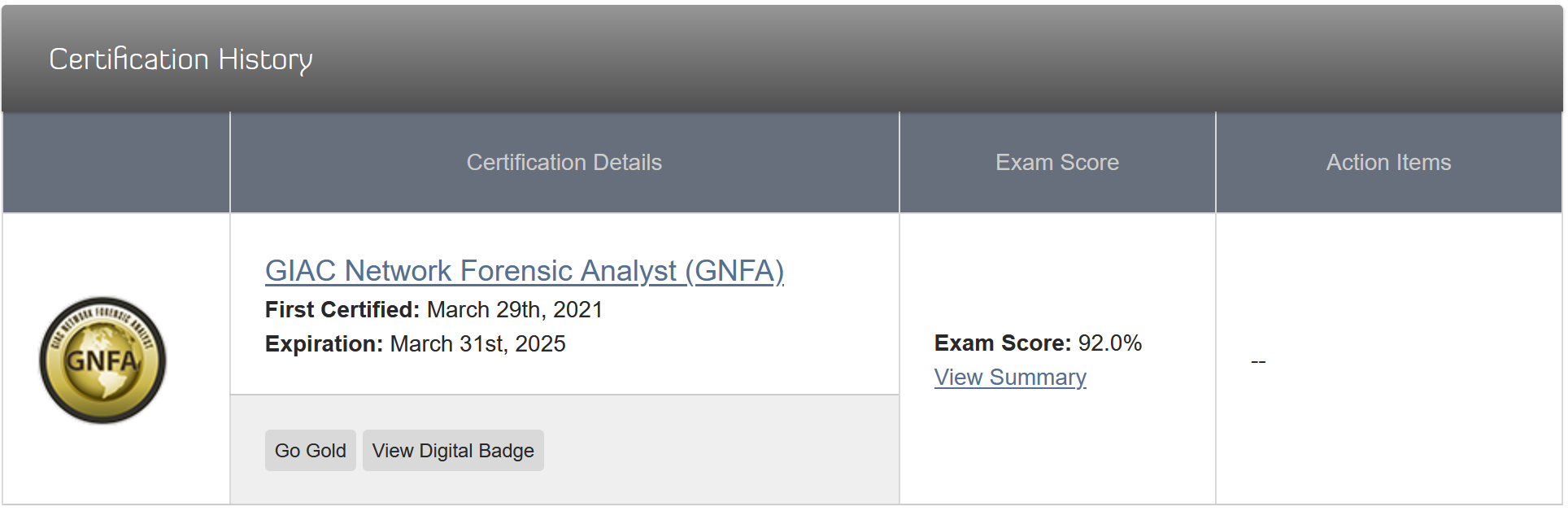
On Monday (March 29, 2021) I passed my GIAC: Network Forensic Analyst certification exam with a 92%. For study resources I used the SANS: FOR572 online video series, slides and books. I didn’t dedicate a ton of time into studying. Infact this probably took me nearly 100 days from the time I purchased the exam attempt and actually taking the exam. Within the 100 days were weeks when I didn’t crack a book or start a video.
SANS FOR572
In the SANS FOR572 series Phil Hagen(@PhilHagen) does a really great job of bringing you up from Zero-to-Hero throughout the course. In my opinion you definitely should have some basic experience in networking, security concepts like boundary defense, and understanding how things look on the wire and how they should look on the wire. If you only have a couple years of good experience in the field, spanning multiple domains, you should have no problem keeping up with the material. If you have less experience, it doesn’t mean you can’t pass the exam but, it may be more difficult. Phil speaks clearly and delivers the material very well, mixed with tales of personal experiences.
While I haven’t been doing incident response or digital forensics at all as part of my day job, I regularly participate in CTF’s chasing flags through an environment or hunting for flags through PCAPs. Most of the tools used throughout the course material I have running in production environments or have running here at my home for network visibility and “research”. I spent most of my career around traditional networking and network security products like firewalls, IPSs, Proxies and more. I understand multi-vendor and multi-capability security stacks well. So, when I saw the tools and concepts Phil Hagen was presenting in the material it felt very comfortable.
The Exam
I come from a Cisco testing background having gone from CCNA to CCIE, I was happy to NOT see what are know in the industry as “Cisco Style Questions” where there are multiple correct answers and you have to pick the most correct answer. Instead, the GIAC: NFA exam was clear and there was a single answer for each question. This alleviates a lot of frustration that can sometimes occur through certification exams. I finished the exam with lots of time to spare.
Testing outline:
- 50 questions
- 2 hours
- Open Book !!!
This was the first exam I’ve ever taken that was an open book test. It was weired and frankly I forgot to reference them throughout the test. There were a few questions where I paused as I was looking over the multiple choice answers and remembered: “Oh right, I can look this up!”, I would thumb through the book to the relevant section and skim and page or two until I could verify my intended answer. Without the books I still would’ve passed but not gotten as high of a score.
Index Method
I did not use the index method. I read as much as I could about this and watched a few ‘how-to’ videos but I just didn’t understand it. I started a spreadsheet but got about 25-rows done and gave up. It’s not for me. I see the value in it so I’m happy it works for many others but it’s not for me.
Practice Exams
I purchased 2 practice exams with my certification attempt. When I was about halfway through the material I took one, just to see if I was ready because frankly I was getting tired of studying and just wanted to get it out of the way. I scored well but ultimately decided to push through all the material before taking my certification attempt. The night before my certification attempt I took my 2nd practice exam and I scored even better. At that point I felt confident I would at least pass the exam, regardless of score. During the practice exams I didn’t use the books very often, 2 or 3 times maybe. I did feel like the practice exams were a good representation of the certification exam. I don’t believe they are from the same question pool, but they are similar so read the questions carefully and look at the diagrams carefully.
Why?
If you don’t do DFIR why take this exam?
I’m not sure why I pursued this as opposed to any other certifications. Personally, I always wanted to be the “anti-hacker”. The guy who could use a bunch of crazy commands CLI filtering to find the needle in the haystack. There’s something about the ‘hunt’ that I love. Also, “Network Forensic Analyst” sounds pretty cool! Ultimately, because I don’t do this everyday for a living, I just wanted a way to learn more, and by pursuing a certification with a proven curriculum of study material seemed the best way to learn.
What did I learn?
I learned a bunch of things. There were some tools that I was unaware of such as: silk, nfdump, and the value of proxy logs. Also, through demonstration and exercises I learned some additional filtering and flags for various CLI tools that I needed more practice on.
The Hug of Thunder
When I started this journey I put a question on on twitter to see who (if anyone) is pursuing a SANS certification other than myself. I received only a few replies but one very important was from Andre. He mentioned he was just starting SEC503. We became daily DM buddies, checking in on each others progress and what we’ve learned. If it wasn’t for this encouragement I might have let this one slip. For the record SEC503 and FOR572 overlap a little bit so we had some common ground between us. I wish him the best on his exam and because of all the great things I’ve heard and seen from the course material, I look forward to completing the SEC503 exam this year too!
Can you pass the cert without the training?
I’m not sure I can weigh in on this. Everyone is different. I even asked this question to Phil Hagan via a Slack we have in common. I think no matter what certification you are going for you should always take the tailored training. I know, in the case of SANS, it’s expensive, but so is failing the exam. It’s a gamble. I say TAKE THE TRAINING, you’ll learn something.
GIAC Advisory Board
Because I scored above a 90% I got an invite to the GIAC Advisory Board. It’s a mailing list with threads related to current events, certifications, and general IT and security focused queries.