Working With Linux Cooked Capture Headers Using TraceWrangler
This outlines how to use TraceWrangler to solve a real world issue when processing PCAPs with multiple interface types.
Published on April 12, 2021 by Tony E.
3 min READ
The Problem
Sometimes when loading a PCAP into various tools you get a cryptic error: an interface has a type 1 different from the type of the first interface. I had one PCAP that would generate various errors in different tools.
The Evidence
Brim:
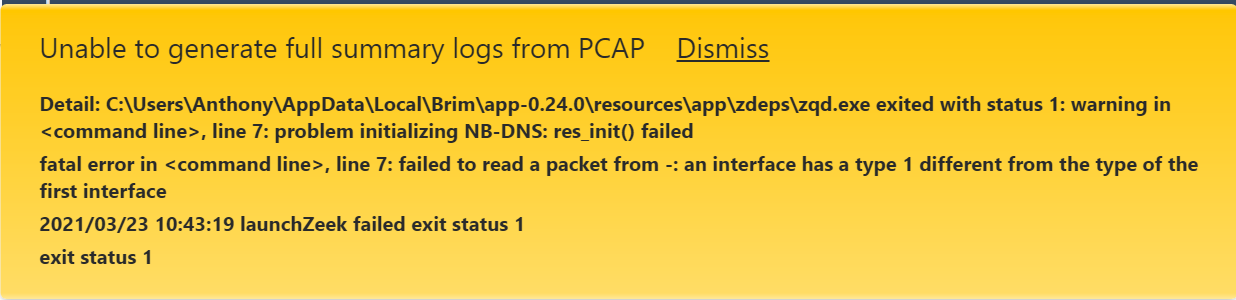
See this Github issue I raised.
Zeek:
root@server:~/ctf$ /opt/zeek/bin/zeek -C -r ctf-dump-v2.pcap
fatal error: failed to read a packet from ctf-dump-v2.pcap: an interface has a type 1 different from the type of the first interface
Suricata:
root@server:~$ suricata -r ctf-dump-v2.pcap -c /etc/suricata/suricata-debian.yaml
10/4/2021 -- 23:10:01 - <Error> - [ERRCODE: SC_ERR_PCAP_DISPATCH(20)] - error code -1 an interface has a type 1 different from the type of the first interface
tcpdump:
root@server:~$ tcpdump -r ctf-dump-v2.pcap
reading from file ctf-dump-v2.pcap, link-type LINUX_SLL (Linux cooked)
tcpdump: pcap_loop: an interface has a type 1 different from the type of the first interface
Wireshark & tshark:
Had no problems reading the PCAP.
The Solution
To fix this issue we need to iterate through the PCAP re-writing the SLL frame headers with standard ethernet headers. Tracewrangler makes quick work of this. The more correct solution is for the application developers to impliment compatibility with this interface type or a mix of interface types in the same PCAP file.
Tracewrangler
Tracewrangler is an awesome tool for manipulating PCAP files. It is written by Jasper Bongertz(@packetjay) and has gotten me out of a few jambs. This tool performs an number of common PCAP file manipulation tasks quickly. For example:
- Add or Remove a VLAN ID in the header
- Mask/re-write the src or dst MAC addresses
- Mask/re-write the src or dst IP addresses
- Slice off the payloads leaving only the headers
- ^^^ Just to name a few, and many many more!!!
Linux Cooked Capture Mode
This is “Linux Cooked Capture Mode” and you can find frames using this header type in your PCAP’s using the Wireshark display filter: sll. This header is 16-bytes and as you can see very different from a standard Ethernet header. Some tools actually don’t have a problem processing PCAP’s which contain only SLL, but most will choke when they contain a mix of various Layer-2 headers(in my case a mix of sll && eth). Frames using Ethernet headers are 14-bytes by default and can be isolated using the Wireshark display filter: eth.
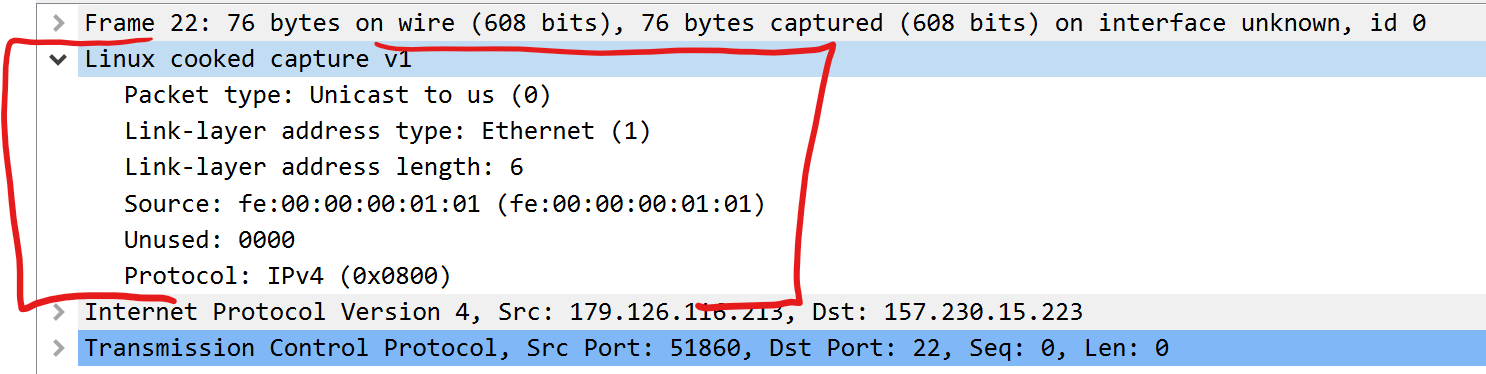 | 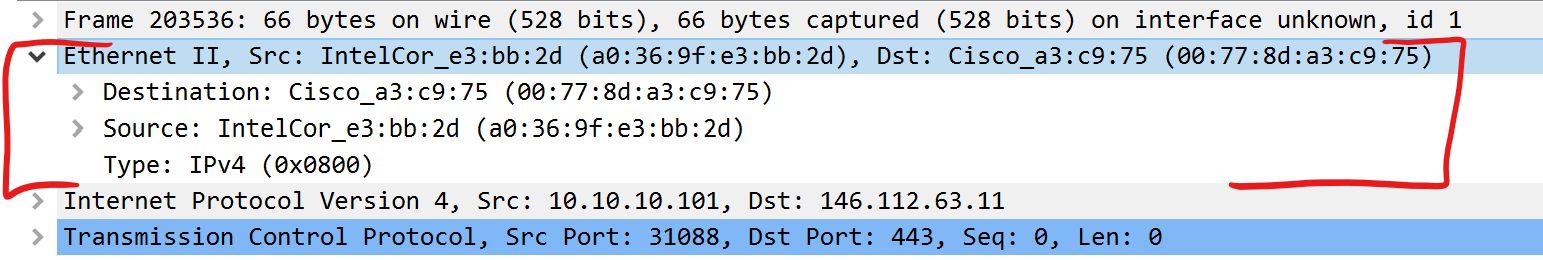 |
NOTE: Alternatively, separate your different layer-2 protocols into seprate PCAPs. Most tools will be okay with this.
Let’s Get To It
Open TraceWrangler click the “Add Files” button and load the PCAP in question.
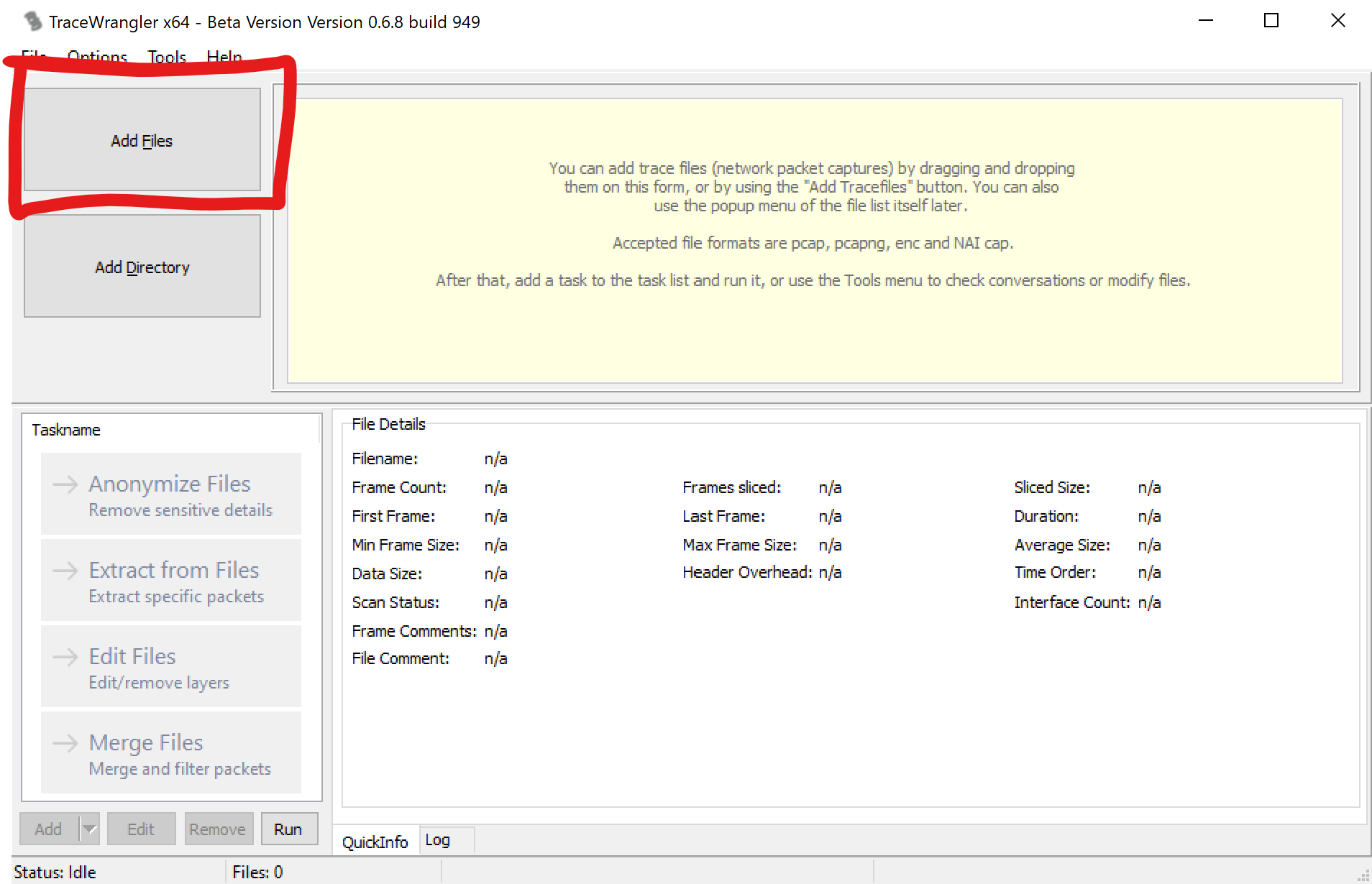
For this particular operation use the “Edit Files” button.
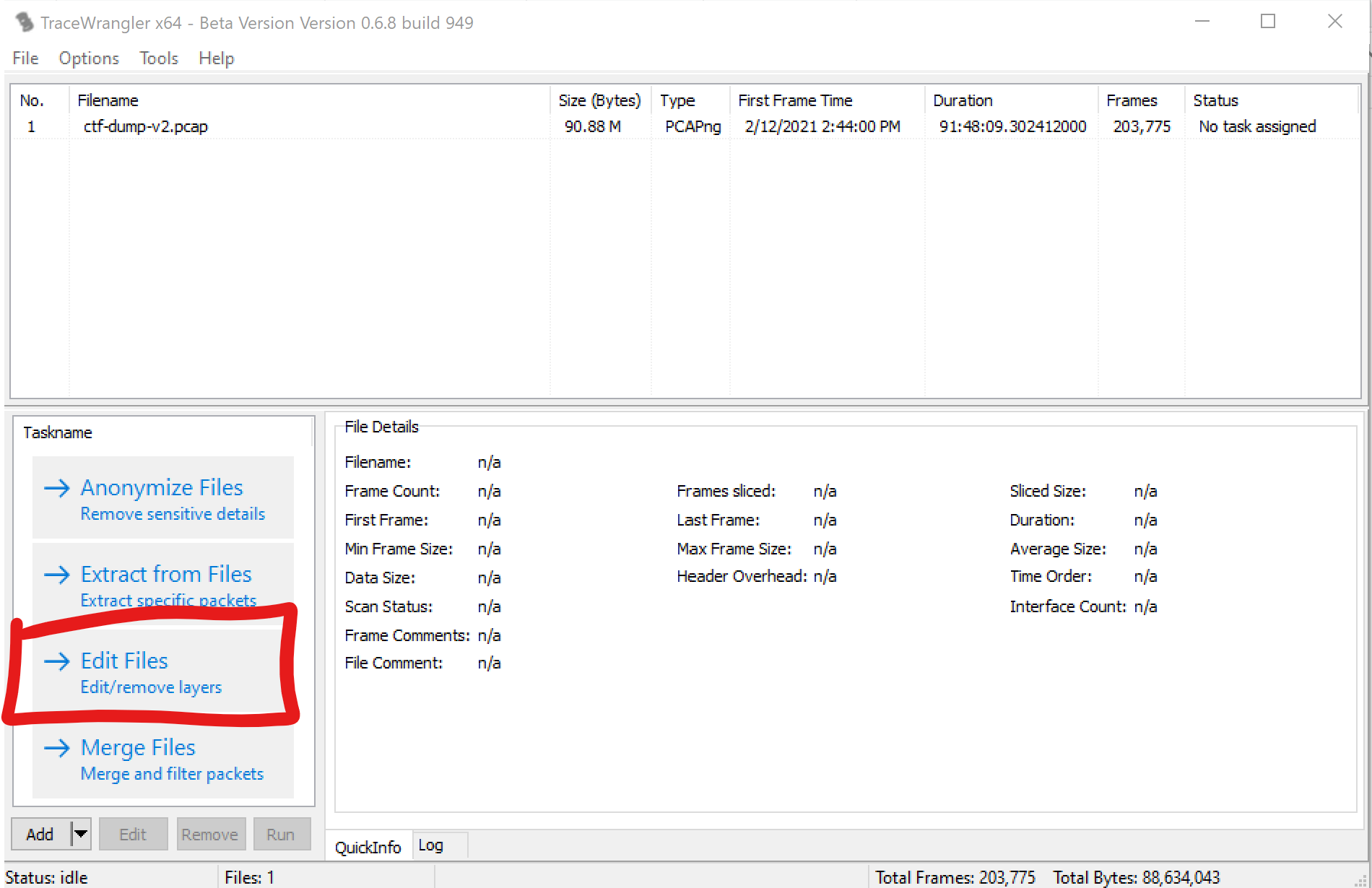
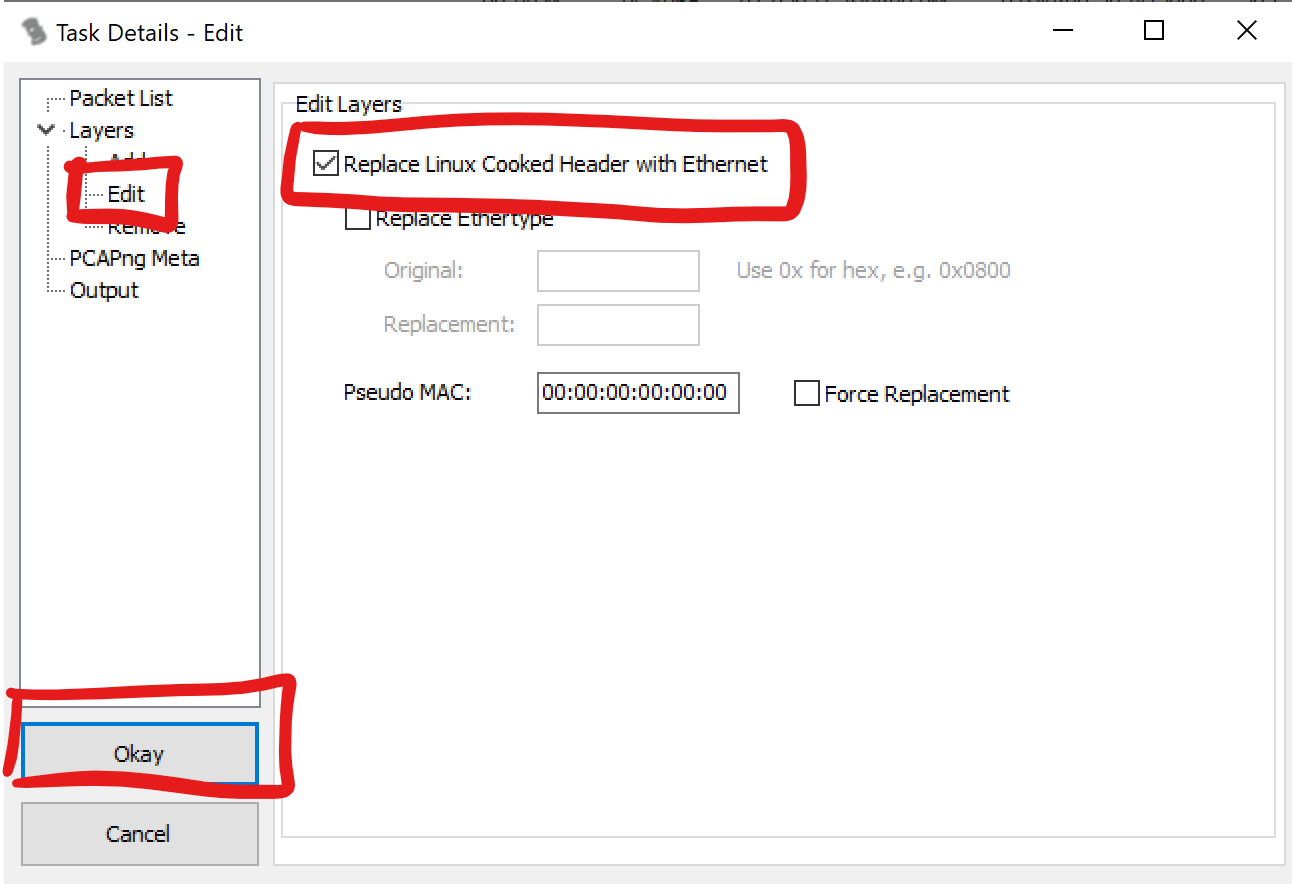
In the navigation tree select “Edit”, Check the box for “Replace Linux Cooked Header with Ethernet” and click “Okay”.
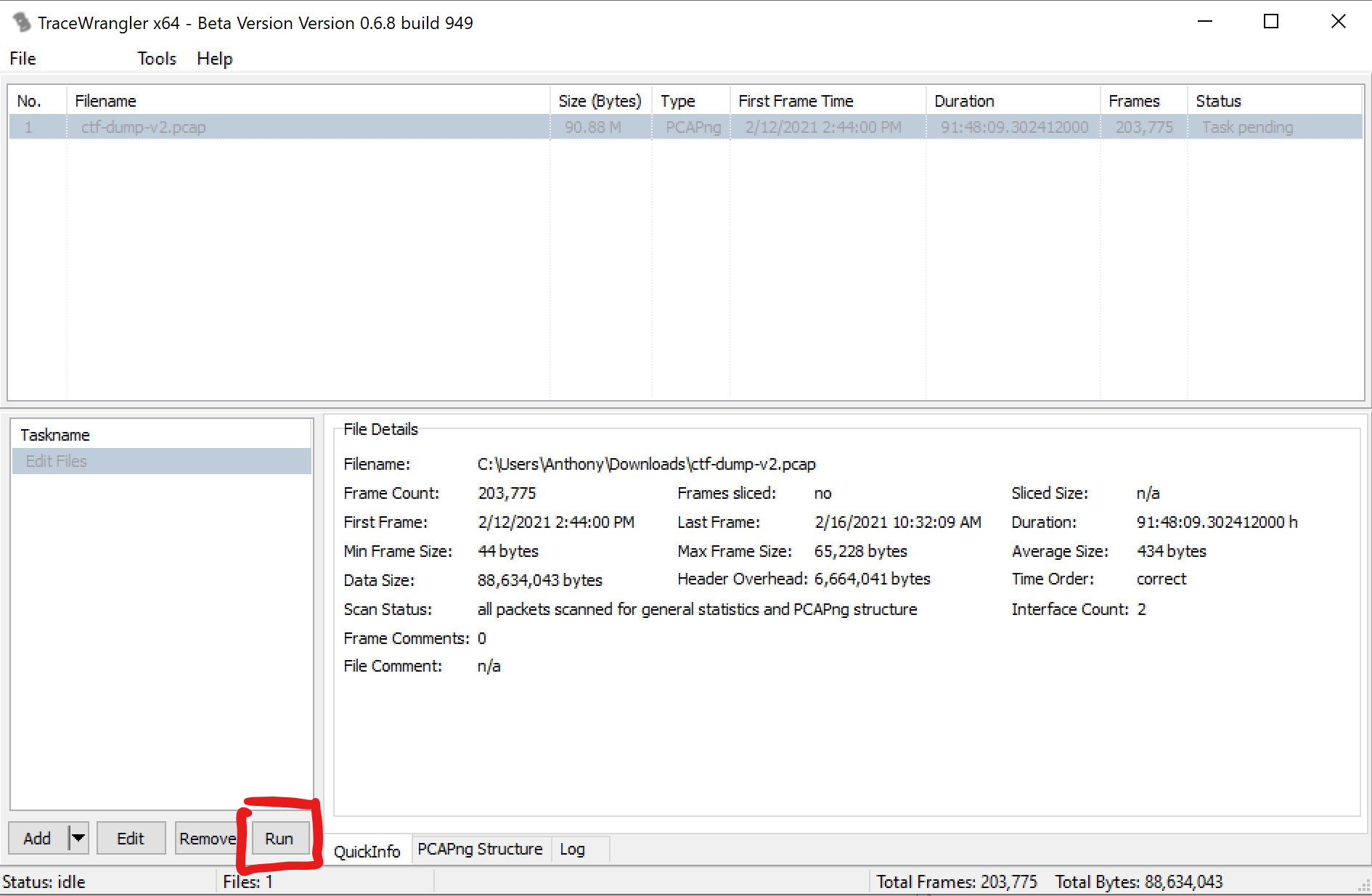
Back on the main TraceWrangler window click “Run” in the bottom left.
Alternative Solution
As mentioned above the root of the problem is the mix of interface types/Layer-2 header types in the same PCAP file. If you separate out the interface types you might be able to process the PCAPs separately. I haven’t found a clean way to accomplish this via CLI yet, I’ll update this blog post if I do.
# Note this doesn't solve the problem but it does seperate out the traffic. however the interfaces are both still listed in the capture properties.
# Even though this doesn't work as expected I'm leaving here as a seed of an idea until I have something better.
tshark.exe -r "c:\Users\Tony\Downloads\ctf-dump-v2.pcap" -w "c:\Users\Tony\Downloads\sll.pcap" -Y "sll"
tshark.exe -r "c:\Users\Tony\Downloads\ctf-dump-v2.pcap" -w "c:\Users\Tony\Downloads\eth.pcap" -Y "eth"